Configuring external network access to ASM
You can configure ASM so users on a public network can access Self Service Portal and the ASM app without needing to log into the corporate network.
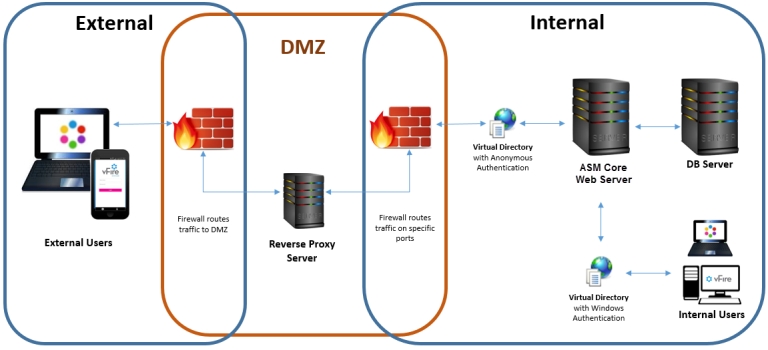
Depending on organizational security requirements, the recommended environment and security configurations may differ. The most common security recommendation is to create a demilitarized zone (DMZ) containing a reverse proxy server buffered by firewalls.
Work with your Network Administration teams to configure reverse proxy servers, DMZ, and IIS redirection.
We outline three DMZ scenarios, based on whether or not Windows Authentication is enabled on the ASM System within the secure network:
DMZ with a web server where ASM Core is installed. The ASM System within the secure network may / may not have Windows Authentication enabled.
For more information, see Option 1: Install a second ASM System on a web server in the DMZ.
DMZ with a reverse proxy server. The ASM System within the secure network has Windows Authentication disabled.
For more information, see Option 2: Set up a Reverse Proxy Server in the DMZ, Authentication Disabled.
DMZ with a reverse proxy server. The ASM System within the secure network has Windows Authentication enabled.
For more information, see Option 3: Set up a Reverse Proxy Server in the DMZ, Authentication Enabled.
Ports to open in the firewalls
Ports
80
443
TCP 1433, UDP 1434
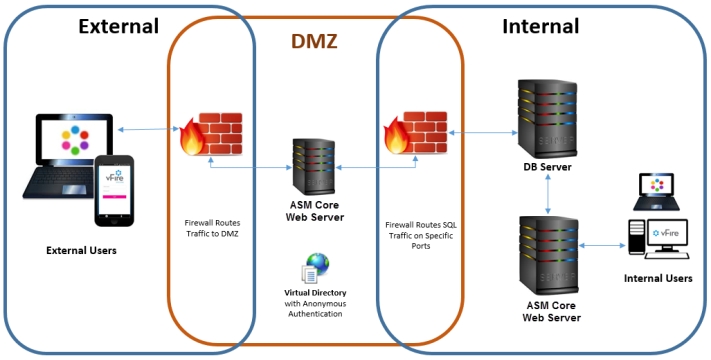
Option 1: Install a second ASM System on a web server in the DMZ
Internal network
Install the primary ASM System on the internal server. You may choose to enable Windows Authentication or not; it has no effect on this configuration.
DMZ
Configure a second web server within the DMZ to act as a reverse proxy server.
On this web server in the DMZ:
Create an ASM System that points to the same database as the internal ASM System.
During system creation, when prompted to update the database, select No
In the virtual directory for this system, disable Windows Authentication and enable Anonymous Authentication.
Stop all ASM Core services and set their "Start Up" property to Manual; except for the ASM Administrative Service.
Ensure the ASM Administrative Service is running and the "Start Up" property is set to Automatic.
Using the registry key, disable the database upgrade via registry string
SkipDatabaseUpgrade = 1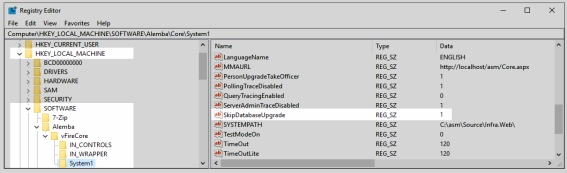
URL for External Users
The URL points to the server and virtual directory within the DMZ.
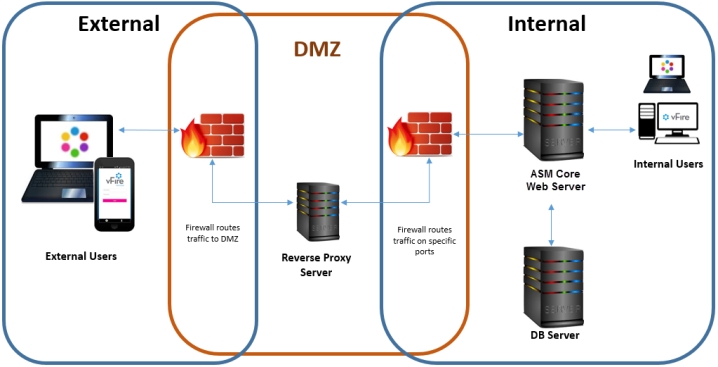
Option 2: Set up a Reverse Proxy Server in the DMZ, Authentication Disabled
Internal network
Install the primary ASM System on the internal server. Do not enable Windows Authentication.
DMZ
Configure a reverse proxy server within the DMZ.
On this server in the DMZ:
Install IIS
Create a virtual directory; disable Windows Authentication and enable Anonymous Authentication
Configure IIS to redirect traffic to the ASM Core application server and virtual directory within the internal secure network.
URL for External Users
The URL points to the reverse proxy server and virtual directory within the DMZ.
Option 3: Set up a Reverse Proxy Server in the DMZ, Authentication Enabled
Internal network
Enable Windows Authentication on the internal server's ASM System.
On the internal server:
Create a second ASM System that points to the same database as the primary ASM System.
During system creation, when prompted to update the database, select No
In the virtual directory for the new system, disable Windows Authentication and enable Anonymous Authentication.
Using the registry key for the new system, disable polling of services via registry string
PollingDisabled = 1Using the registry key for the new system, disable the database upgrade via registry string
SkipDatabaseUpgrade = 1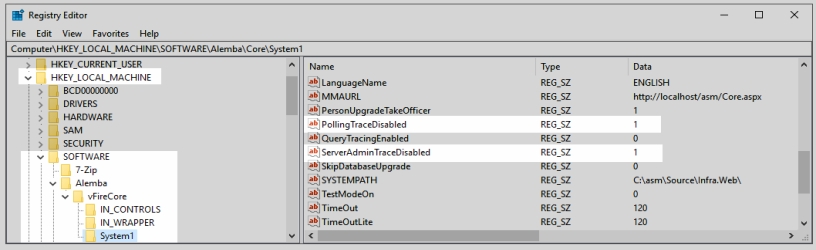
DMZ
Configure a reverse proxy server within the DMZ.
On this server in the DMZ:
Install IIS
Create a virtual directory; disable Windows Authentication and enable Anonymous Authentication
Configure IIS to redirect traffic to the internal application server and the virtual directory that has Anonymous Authentication enabled
URL for External Users
The URL points to the reverse proxy server and virtual directory within the DMZ.
Was this helpful?
