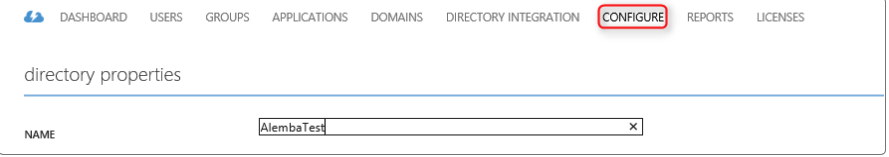
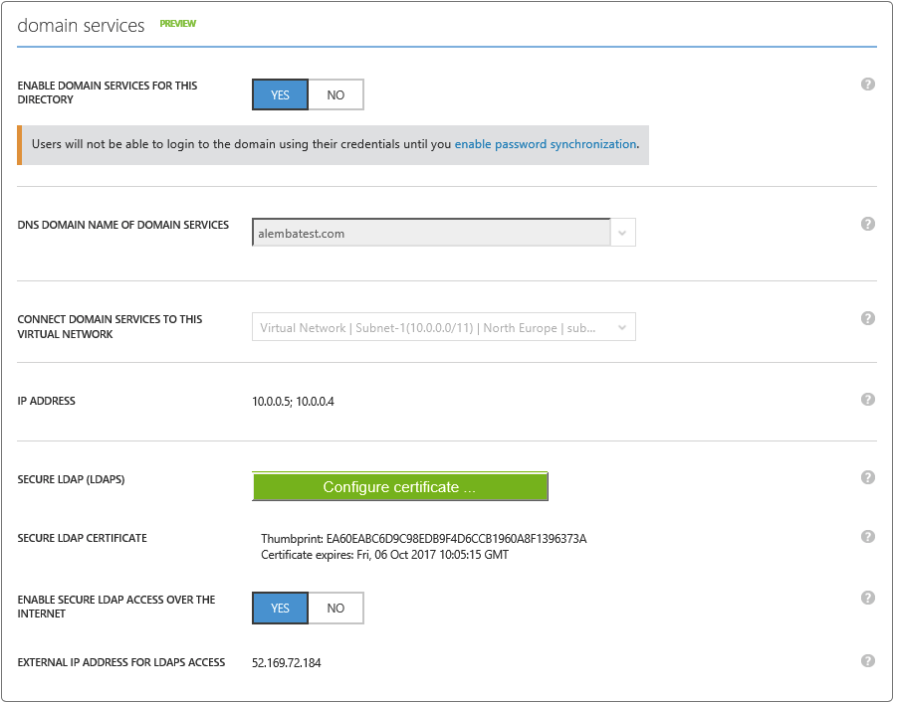
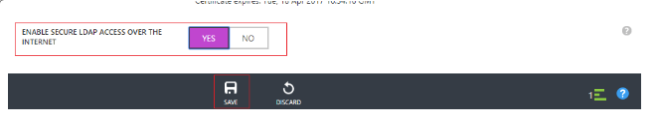
Configuring Azure Active Directory discovery
This topic describes how to configure Azure Active Directory discovery through Secure Lightweight Directory Access Protocol (TLS 1.2).
Configuring ASM Core
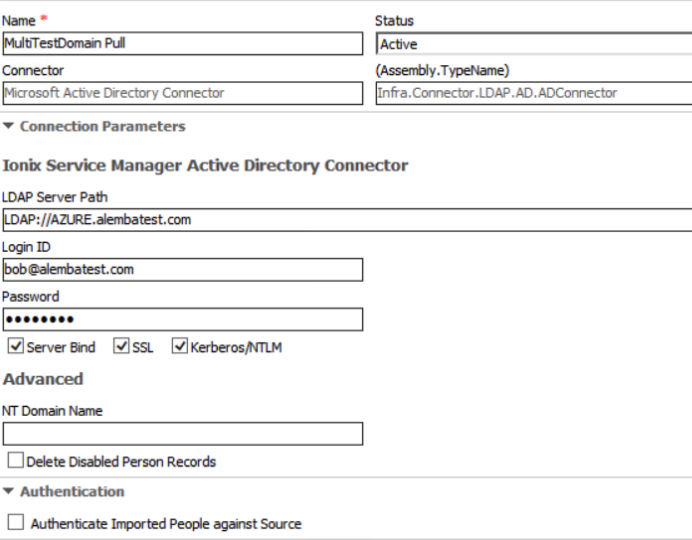
Configuring Azure Active Directory.