Partitioning
Partitioning enables you to divide your system into separate functional areas.
Partitioning is a way of dividing items in your database into separate sections in order to set up different Service Desk, Workflow Management and CMDB options for different functional units. It provides a means of true Enterprise Service Management (ESM) where field level security and other system settings will not suffice. Sometimes, regulatory mandates require a secure partition for certain areas of support and service management. This is common in health care and banking.
Alemba recommends that you see your professional services consultant or your account manager for help deciding what is right for you.
Partitioning effectively creates secure, separate, but shared ASM systems (certain data, such as people and locations, can be shared across partitions) without actually creating separate enterprise ASM systems. This means there is no need for the additional cost, infrastructure, and maintenance that adding additional copies of ASM would ordinarily incur. You can have as many partitions as you want. There are no additional fees or maintenance and support costs.
For example, an organization’s Service Desk can have multiple support groups responsible for a wide variety of unrelated systems, technologies and User support. They may or may not share a common user-base and organizational structure. Each support group requires its own issue types and service levels for different organizations and Users, as well as different escalation response times. In addition, the configuration items supported by each group may be of no interest to other groups. They are effectively separate support groups entirely, such as one might encounter with a 3rd party support provider or MPO. While this could be handled with field level security and system settings, some organizations providing support in this manner may prefer the physical separation partitioning provides.
In another example, a hospital must maintain strict security over the health records of its patients. The service and support for Epic, EpicShare, EpicResearch, Cosmos, MyChart, and EpicUserWeb system tickets and patient related inquiries and assistance may contain sensitive patient health record data and only certain analysts are permitted access.
The hospital chose to partition its Epic family of support services and all related patient and ticket data into a "Patient Support Services" partition. All other IT Service and Support for the hospital is held in the "IT" partition and much of the common data is not partitioned. This satisfies HIPAA (a federal law that required the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge), and JCAHO oversight (an accreditation body responsible for healthcare delivery).
With partitioning, the organization only needs to maintain one database, with only the information relevant to Analysts and Users of a particular partition being accessible to them. On the other hand, non-partitioned information can be accessed and updated by all analysts with security access rights to do so.
By partitioning, an organization using a single database server can benefit from:
simplified and centralized administration
a single consistent User and organizational listing
groups having independent types and/or escalation times
easy monitoring by senior management across support groups
consolidation of reporting
a smaller, partitioned Knowledge Bank, reducing the time spent looking through search results.
The Implications of Partitioning
Partitioning needs careful planning as it has implications when calls, requests, and tasks are forwarded within different partitions.
For example, an Analyst logging a call may attach a CI created in a different partition to the call and forward it to an Analyst who does not have access to the partition in which the CI has been created, making it difficult for the receiving Analyst to complete their role in resolving the call. It is therefore important that you plan how you want to partition your system before you set up partitioning.
Once partitioning has been applied it cannot easily be turned off without technical assistance. If you decide to do so, contact Alemba Support for assistance, as it may have a significant impact on the way in which your system functions.
Analyst Visibility of Calls in other Partitions by Organization
Analysts in Core can search and find all Calls, Requests and Tasks in their organization, irrespective of which partition the call is in.
An Analyst with Review Org Calls/Requests/Tasks selected in their IPK/Workflow Management Security Roles can view any Calls/Requests/Tasks within their Organization (that which is in their Person Record) irrespective of which partition the call is currently in, and irrespective of which partitions the Analyst has been given access to.
System Administration
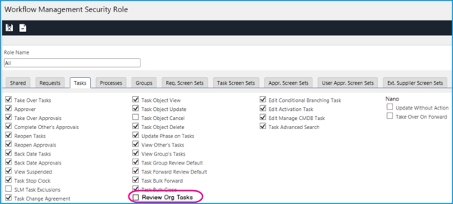
IPK Management Security Role: Review Org Calls - ON.
When Review Org Calls is selected, the analyst will have View Access to calls in other partitions where the organization on the call matches that of the analysts person record.
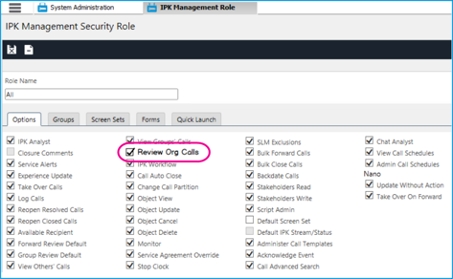
Workflow Management Security Role: Review Org Requests - ON.
When Review Org Requests is selected the analyst have View Access to requests in other partitions where the Organization on a request matches that of the Analyst’s Person Record.
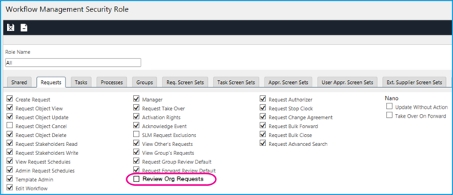
Workflow Management Security Role -> Tasks Tab: Review Org Tasks - On.
When Review Org Tasks is selected the analyst have VIEW ACCESS to tasks in other partitions where the Organization on a task matches that of the Analyst’s Person Record.
What View Access Permits the Analyst to Do
Search for and open the Call/Request/Task
View History of the Call/Request/Task
View Objects on the Call/Request/Task
What View Access Does not Permit the Analyst to Do
Take Action/Ownership of the Call/Request/Task
Add Notes to the Call/Request/Task
Add Objects to the Call/Request/Task
Edit the Call/Request/Task
Delete Objects on the Call/Request/Task
Partitioning Behavior
A call can either be in the analyst’s partition or not.
A call can either be in the same organization as the analyst or not.
These two conditions are mutually exclusive.
Example Scenario: Analyst Emma has access to Partition A and is in Organization 1.
The call conditions can match that of the axes, for example, the call can be:
In Org 1 and Partition A or,
In Org 1 and Partition B or,
In Org 2 and Partition A or,
In Org 2 and Partition B
The combination will determine the access Emma has to the call.
Partition A
Partition B
Org - 1
Edit Access
View Access
Org - 2
Edit Access
No Access
Example Scenario
Call 123 has been logged by a user in the Self-Service Portal in Partition A.
The user is in Organization 1, as is Analyst Emma.
Analyst Emma, has taken action and is reviewing the call. She decides to send it to another group to take further. The other group belongs in a partition to which Emma does not have access. The partition of the call changes from A to B.
The user contacts Emma and asks for an update on the call. The Organization linked to the call is that of the user – Org -1.
With Review Org Calls selected in her IPK Management Security role, Emma is able to search for and view the details of Call 123.
**Emma is not able to Take Back, or Take Action on the call as it is in a partition to which she does not have access but she can view all of the call details, add notes or attachments.
Last updated
Was this helpful?
